

Getty Photographs
Researchers have unearthed never-before-seen malware that hackers from North Korea have been utilizing to surreptitiously read and obtain electronic mail and attachments from contaminated customers’ Gmail and AOL accounts.
The malware, dubbed SHARPEXT by researchers from safety agency Volexity, makes use of clever means to set up a browser extension for the Chrome and Edge browsers, Volexity reported in a weblog publish. The extension cannot be detected by the e-mail providers, and because the browser has already been authenticated utilizing any multifactor authentication protections in place, this more and more well-liked safety measure performs no function in reining within the account compromise.
The malware has been in use for “nicely over a 12 months,” Volexity stated, and is the work of a hacking group the corporate tracks as SharpTongue. The group is sponsored by North Korea’s authorities and overlaps with a group tracked as Kimsuky by different researchers. SHARPEXT is concentrating on organizations within the US, Europe, and South Korea that work on nuclear weapons and different points North Korea deems vital to its nationwide safety.
Volexity President Steven Adair stated in an electronic mail that the extension will get put in “by way of spear phishing and social engineering the place the sufferer is fooled into opening a malicious doc. Beforehand we have seen DPRK menace actors launch spear phishing assaults the place all the goal was to get the sufferer to set up a browser extension vs it being a publish exploitation mechanism for persistence and knowledge theft.” In its present incarnation, the malware works solely on Home windows, however Adair stated there is no cause it could not be broadened to infect browsers working on macOS or Linux, too.
The weblog publish added: “Volexity’s personal visibility exhibits the extension has been fairly profitable, as logs obtained by Volexity present the attacker was ready to efficiently steal 1000’s of emails from a number of victims by way of the malware’s deployment.”
Putting in a browser extension throughout a phishing operation with out the end-user noticing is not straightforward. SHARPEXT builders have clearly paid consideration to analysis like what’s printed right here, right here, and right here, which exhibits how a safety mechanism within the Chromium browser engine prevents malware from making adjustments to delicate consumer settings. Every time a official change is made, the browser takes a cryptographic hash of among the code. At startup, the browser verifies the hashes, and if any of them do not match, the browser requests the previous settings be restored.
For attackers to work round this safety, they need to first extract the next from the pc they’re compromising:
- A replica of the assets.pak file from the browser (which accommodates the HMAC seed utilized by Chrome)
- The consumer’s S-ID worth
- The unique Preferences and Safe Preferences information from the consumer’s system
After modifying the choice information, SHARPEXT routinely hundreds the extension and executes a PowerShell script that permits DevTools, a setting that permits the browser to run custom-made code and settings.
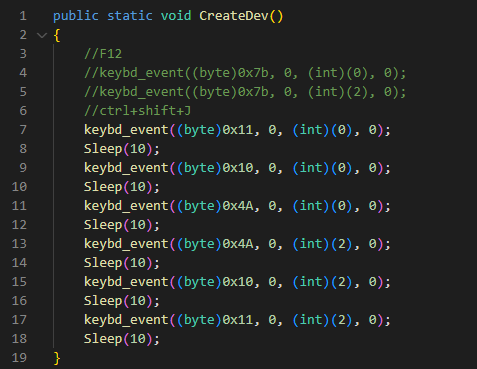
“The script runs in an infinite loop checking for processes related to the focused browsers,” Volexity defined. “If any focused browsers are discovered working, the script checks the title of the tab for a particular key phrase (for instance’ 05101190,’ or ‘Tab+’ relying on the SHARPEXT model). The particular key phrase is inserted into the title by the malicious extension when an lively tab adjustments or when a web page is loaded.”
Volexity
The publish continued:
The keystrokes despatched are equal to
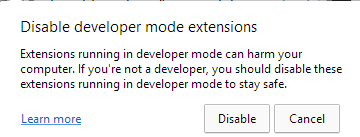
Management+Shift+J, the shortcut to allow the DevTools panel. Lastly, the PowerShell script hides the newly opened DevTools window through the use of the ShowWindow() API and theSW_HIDEflag. On the finish of this course of, DevTools is enabled on the lively tab, however the window is hidden.As well as, this script is used to conceal any home windows that would alert the sufferer. Microsoft Edge, for instance, periodically shows a warning message to the consumer (Determine 5) if extensions are working in developer mode. The script continually checks if this window seems and hides it through the use of the
ShowWindow()and theSW_HIDEflag.
Volexity
As soon as put in, the extension can carry out the next requests:
| HTTP POST Information | Description |
| mode=checklist | Listing beforehand collected electronic mail from the sufferer to guarantee duplicates will not be uploaded. This checklist is repeatedly up to date as SHARPEXT executes. |
| mode=area | Listing electronic mail domains with which the sufferer has beforehand communicated. This checklist is repeatedly up to date as SHARPEXT executes. |
| mode=black | Accumulate a blacklist of electronic mail senders that must be ignored when gathering electronic mail from the sufferer. |
| mode=newD&d=[data] | Add a area to the checklist of all domains seen by the sufferer. |
| mode=connect&title=[data]&idx=[data]&physique=[data] | Add a new attachment to the distant server. |
| mode=new&mid=[data]&mbody=[data] | Add Gmail knowledge to the distant server. |
| mode=attlist | Commented by the attacker; obtain an attachments checklist to be exfiltrated. |
| mode=new_aol&mid=[data]&mbody=[data] | Add AOL knowledge to the distant server. |
SHARPEXT permits the hackers to create lists of electronic mail addresses to ignore and to hold monitor of electronic mail or attachments that have already been stolen.
Volexity created the next abstract of the orchestration of the assorted SHARPEXT parts it analyzed:

Volexity
The weblog publish gives photographs, file names, and different indicators that educated individuals can use to decide in the event that they have been focused or contaminated by this malware. The corporate warned that the menace it poses has grown over time and is not possible to go away anytime quickly.
“When Volexity first encountered SHARPEXT, it appeared to be a device in early growth containing quite a few bugs, a sign the device was immature,” the corporate stated. “The most recent updates and ongoing upkeep exhibit the attacker is reaching its objectives, discovering worth in persevering with to refine it.”